Debian Security
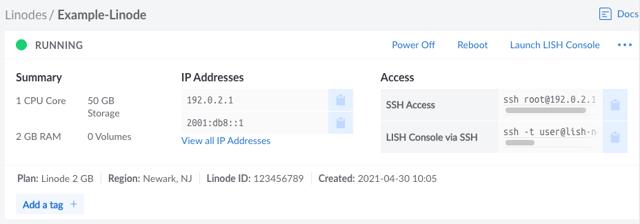
Setting Up and Securing a Compute Instance
After you have successfully created a Compute Instance, there are a few initial configuration steps you should perform within your new Linux system.
Get Started with nftables
nftables replaces the successful iptables and its related frameworks built on Netfilter. With nftables come improvements to performance and usability, but also significant changes to syntax and usage.

Securing MySQL Server
MySQLMySQL is an open-source relational database management system. This guide will show you how to secure and audit a MySQL server.
Cloud Firewall
Linode’s Cloud Firewall service is a robust cloud-based firewall solution available at no additional charge for Linode customers.

Anti-Virus and Rootkit Protection with ClamAV and rkhunter
Anti-virus and Rootkit DetectionThis guide teaches you how to use ClamAV, ClamTK, and rkhunter for anti-virus and rootkit detection to secure your server.

Install SELinux on Debian 10
Ubuntu has a Mandatory Access Control (MAC) system similar to SELinux, named AppArmor. Both SELinux and AppArmor provide a set of tools to isolate applications from each other to protect the host system from being compromised.

How to Configure a Firewall with UFW
What is UFW?UFW, or uncomplicated firewall, is a frontend for managing firewall rules in Arch Linux, Debian, or Ubuntu.

Using Fail2ban to Secure Your Server
What is Fail2Ban Fail2ban is a log-parsing application that monitors system logs for symptoms of an automated attack on your Linode.
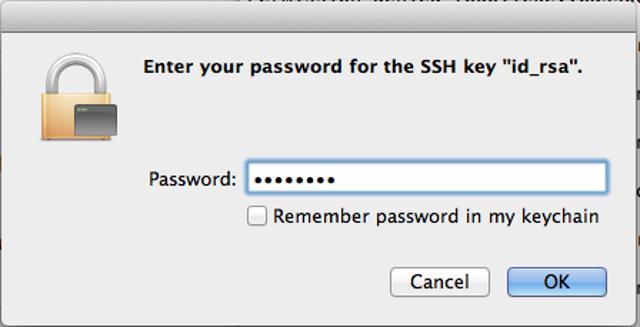
Use SSH Public Key Authentication on Linux, macOS, and Windows
Public key authentication with SSH (Secure Shell) is a method in which you generate and store on your computer a pair of cryptographic keys and then configure your server to recognize and accept your keys.
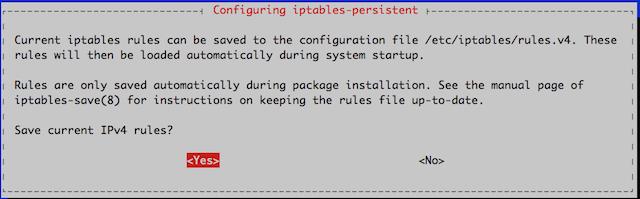
A Tutorial for Controlling Network Traffic with iptables
iptables is an application that allows users to configure specific rules that will be enforced by the kernel’s netfilter framework.

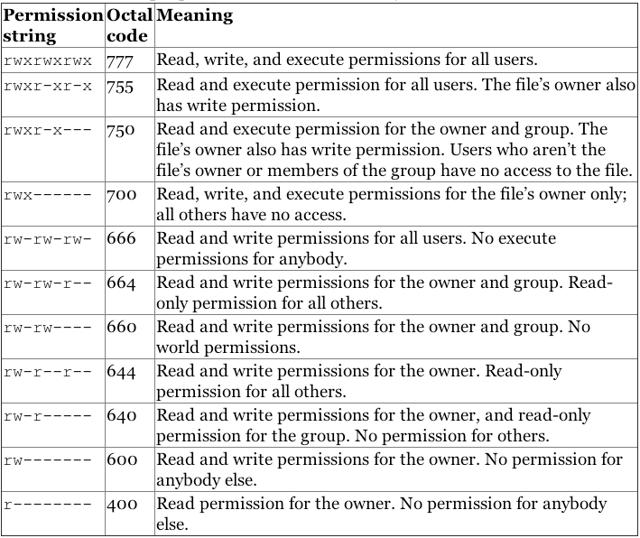
Modify File Permissions with chmod
Modify File Permissions with chmodThe chmod command allows users to change read and write permissions in Unix systems.
Linux Users and Groups
If you are new to Linux/Unix, then the concept of permissions may be confusing. This guide provides you with an explanation of what permissions are, how they work, and how to manage them.
