이제 모든 Linode 고객이 고급 DDoS 보호를 사용할 수 있으며 무료임을 발표하게 되어 기쁩니다. Linode DDoS를 사용하면 분산 서비스 거부 (DDoS) 공격으로 인한 예상치 못한 다운 타임과 대기 시간으로부터 서버와 애플리케이션을 보호할 수 있습니다.
차세대 네트워크에 의해 구동되는 이 추가 보호 계층은 상시 가동되고 완전 자동화되며 고급 기계 학습 및 규칙 기반 접근 방식을 적용하여 악성 트래픽을 지능적으로 차단합니다.
작동 원리
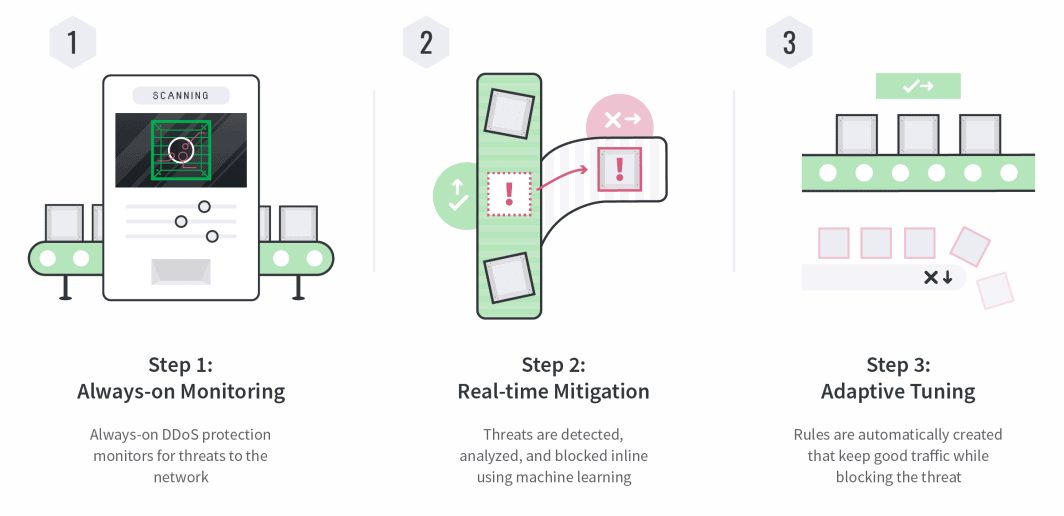
Linode에서는 고객에게 중요한 것에 투자합니다. DDoS 보호를 사용하면 Linode 클라우드 경험에 지연 시간을 추가하지 않고도 확신을 가지고 확장하고 의도하지 않은 다운 타임을 방지할 수 있습니다.
여기에서 발표에 대해 자세히 읽어보거나 linode.com/ddos를 방문하십시오.








댓글 (17)
This feature is terrible for users here in brazil. We are having lots of instability acessing websites/ips hosted on linode and EVEN THE login page of customer is very unstable. Terrible feature.
Hey Gil, our DDoS protection would serve to prevent disruptive network attacks on our customers and infrastructure, which would improve stability and accessibility.
If you’re experiencing connection issues to our services, we’d like to investigate for issues on our end and help resolve them. Accordingly, please open a Support ticket with details of the service disruptions you’re seeing, including relevant MTR reports in both directions with the flags “-rwzbc100”. Feel free to respond here with a ticket number and we’ll look at it right away.
This shouldn’t affect your access to websites hosted on Linode unless you are sharing a network with some unsavory systems.
How many Gb/s protection does this provide?
I can’t talk about specific numbers, but I can say that the way we mitigate and adapt to attacks in real time allows us to handle DoS attacks on a global scale.
Is it enabled by default on all linodes ( including at cloudways ) ?
Yes, DDoS protection applies to all Linodes, including those provisioned through Cloudways. There’s no need to adjust your settings in order to activate it.
Will there be an option to toggle, ON/OFF within the Cloud Firewall?
Hey Carl, just want to clarify that our advanced DDoS protection (which is always on) is distinct from our anticipated Cloud Firewall offering, which we’re aiming to release in 2020. I can’t give any exact details for the Cloud Firewall service yet, but it will certainly be configurable and geared towards ease of use.
Given that, I’ve updated our internal tracker with your request. If there are any other specific features you’d like to see in our Cloud Firewall offering, a great place to send requests would be at feedback@linode.com — be sure to include as many details as possible as well as the reason or use case for the feature requested.
where do I get more info about the ddos events\rules? how do I see if I am under attack or who get blocked? how many get blocked? etc..
I am sure we gonna have some false positive so like said before we need some more control over that, but great job this and the cloud firewall(which I am really waiting for) will place you in a good position
I’m glad to hear you’re as excited about Cloud Firewalls as we are. When Cloud Firewalls are available, you’ll have the ability to configure them. With our advanced DDoS protection, customers won’t be able to control the traffic that is blocked or getting through. The rules for DDoS protection is not publicly available for security reasons.
With this service, our goal is for customers to be unaware of an attack. The malicious traffic will mitigated before it can affect their Linode. This will also protect neighboring Linodes that are on the same host. You will be able to continue to be able to view any traffic that is getting to your Linode, which you’ll be able to mitigate with firewall rules or investigate it with a tcpdump.
we are talking about layer7 also? if yes I dont see how it can be working without a whitelist method
That’s an excellent question, Amir. This service will not protect against smaller layer 7 attacks. You will still need to protect your Linodes at the application level.
Unaware of an attack?
I want to know about any attacks, including DDOS-es, and i have multiple reasons for that.
Also i want to be able to opt out. Similar offerings sometime do more damage than good, and i clearly want the possibility to opt out.
“Will not protect against smaller layer 7 attacks ” – So can protect against big layer 7 attacks ? So whenever i have a problem ( something not working as imagined) , i will need to bug Linode support about the DDOS protection, asking if maybe interferes with our traffic ?
It seems a great feature for small clients, simple setups. But not that great for others.
Thank you for providing us your feedback, especially the reasons why you would want to opt-out of this service. I’ve passed along your comments to our team, including adding the ability to notify customers of possible attacks. If there’s anything additional you would like to add, you can direct it to feedback@linode.com.
Right now, we aren’t providing an opt-out to protect not just your services, but neighboring servers.
This service is designed to protect the application layer from a range of DDoS attack methods, including UDP, SYN and HTTP floods, but it is not a stateful firewall. It will not filter out small amounts of this traffic, which is why you’ll want to secure your Linode.
While we’re always happy to assist our customers, that are tools available to you to be empowered to review networking traffic issues.
I would recommend checking connections between any two endpoints with an MTR report. This will identify where packet loss is occurring. Our Support team is here 24/7 to review MTR reports and empowered to act on behalf of our customers.
I wasn’t talking about about packet loss.
I was talking about layer 7 trouble shooting .
If one of our clients/dev/whatever calls us for example : we respond to all HTTP GET requests, but we don’t answer any HTTP POSTS. Then while i’m debugging , will i need to bug Linode support if the DDOS protection filters out all the POST’s ( DDOS protection assuming its a DDOS ) ?
I really liked that we received raw traffic on Linode
I completely understand your concern. While we don’t anticipate it filtering any legitimate layer 7 traffic, if it seems like it is please reach out to us so we can take a look and evaluate the situation.
Like Pat mentioned, we’ll pass your feedback along to the team regarding the ability to opt-out and your wish to be notified of all potential DDoS attacks, even the smaller Layer 7 ones.