Os NodeBalancers sempre suportaram protocolos baseados em TCP, incluindo SSL - mas temos o prazer de anunciar que os NodeBalancers agora incluem suporte nativo a HTTPS.
Isto significa que um NodeBalancer pode terminar as conexões SSL para você, e ter a funcionalidade e o comportamento que você já desfruta do modo HTTP - incluindo a configuração correta de um X-Fowarded-For com o endereço IP do requisitante e cookies de sessão para a aderência do nó de backend.
Para isso, crie um novo perfil de configuração usando a porta 443 (normalmente), defina o Protocolo para HTTPS e, em seguida, forneça o certificado e sua chave privada (sem uma frase-chave). Certificados intermediários encadeados também são suportados. Aqui está uma imagem de tela mostrando as novas opções:
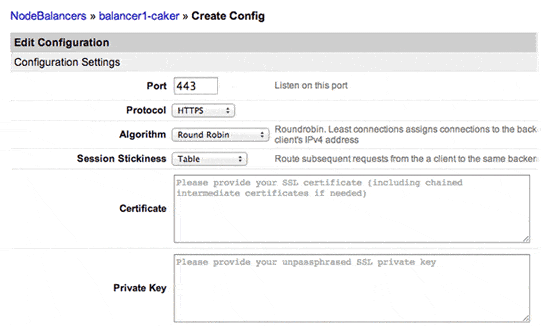
Uma nota para sites SSL de maior tráfego: a negociação SSL é uma operação computacionalmente cara, e a capacidade de um NodeBalancer em modo SSL de se manter atualizado pode não ser suficiente. Nessas situações, recomendamos usar o modo TCP e distribuir a carga de terminação SSL para os seus Linodes backend. Alternativamente, você poderia usar vários NodeBalancers em modo SSL e usar DNS round-robin.
Mais informações:
Aproveite!







Comentários (10)
Does Linode use HAProxy to run this service?
Hi,
If not good for high traffic, what’s the advantage ?
Thanks
@Jan: convenience – it’s very easy to get SSL working using the NodeBalancer user interface. This is also a good first step for us supporting native SSL — we gotta start somewhere.
How computationally expensive is SSL for you guys?
From Google: “On our production frontend machines, SSL/TLS accounts for less than 1% of the CPU load, less than 10KB of memory per connection and less than 2% of network overhead.” (https://www.imperialviolet.org/2010/06/25/overclocking-ssl.html)
What kind of maximum concurrency are we talking about here for SSL on a nodebalancer?
What traffic max rate is expected to be handled by these balancers? If a regular balancer handles 10k, what about SSL ones?
NodeBalancers have a 10,000 concurrent connection limit. It’s not a request/sec limit. There is no artificial request/sec limit built into NodeBalancers. A NodeBalancer config in TCP or HTTP mode can accept connections pretty much as fast as packets can be slung to/from the backends. In other words: it’s a lot.
A NodeBalancer config in HTTPS mode can achieve 10,000 concurrent connections, too – it may just take some time to ramp up to that. While testing very small requests (connections don’t live long) we’ve seen about 150 req/sec via HTTPS mode. Again, it’s a good place to start, and we’ll be working on improving the req/sec throughput of native HTTPS mode.
Thanks for the comments 🙂
Hi. I previously asked if Linode uses HAProxy for this service? (And indirectly I guess I was wondering what other software/hardware is being use. My post is still awaiting moderation even though posts made after mine have been approved.
In the past Linode has been quite open about its architecture, especially about its implementation of Xen. Is there a reason we don’t get much detail about how NodeBalancers work? Is there something offensive or inappropriate about me asking these things?
Tom, I’d be interested too… Although it’s not out of the realm of possibility that they built their own with something like Golang (esp since 1.1), an accounting proxy would be trivial on such stack.
Any chance to have TLS renegotiation so we can host more than one domain on HTTPS ?