NodeBalancers have always supported TCP-based protocols, including SSL – but we’re pleased to announce that NodeBalancers now include native HTTPS support.
This means a NodeBalancer can terminate SSL connections for you, and have the functionality and behavior you already enjoy from HTTP mode – including correctly setting an X-Fowarded-For header with the requester’s IP address, and session cookies for backend node stickiness.
In order to do this, create a new configuration profile using port 443 (typically), set the Protocol to HTTPS, and then provide the certificate and its private key (without a passphrase). Chained intermediate certificates are also supported. Here’s a screenshot showing the new options:
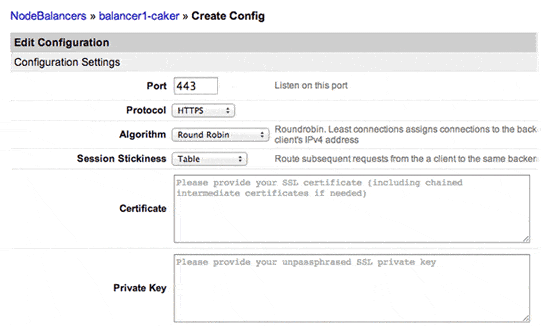
A note for higher trafficked SSL sites: SSL negotiation is a computationally expensive operation, and the ability for a NodeBalancer in SSL mode to keep up may not be sufficient. In these situations we recommend using TCP mode and distributing the SSL termination load to your backend Linodes. Alternatively, you could use multiple NodeBalancers in SSL mode and use round-robin DNS.
More information:
Enjoy!







Comments (10)
Does Linode use HAProxy to run this service?
Hi,
If not good for high traffic, what’s the advantage ?
Thanks
@Jan: convenience – it’s very easy to get SSL working using the NodeBalancer user interface. This is also a good first step for us supporting native SSL — we gotta start somewhere.
How computationally expensive is SSL for you guys?
From Google: “On our production frontend machines, SSL/TLS accounts for less than 1% of the CPU load, less than 10KB of memory per connection and less than 2% of network overhead.” (https://www.imperialviolet.org/2010/06/25/overclocking-ssl.html)
What kind of maximum concurrency are we talking about here for SSL on a nodebalancer?
What traffic max rate is expected to be handled by these balancers? If a regular balancer handles 10k, what about SSL ones?
NodeBalancers have a 10,000 concurrent connection limit. It’s not a request/sec limit. There is no artificial request/sec limit built into NodeBalancers. A NodeBalancer config in TCP or HTTP mode can accept connections pretty much as fast as packets can be slung to/from the backends. In other words: it’s a lot.
A NodeBalancer config in HTTPS mode can achieve 10,000 concurrent connections, too – it may just take some time to ramp up to that. While testing very small requests (connections don’t live long) we’ve seen about 150 req/sec via HTTPS mode. Again, it’s a good place to start, and we’ll be working on improving the req/sec throughput of native HTTPS mode.
Thanks for the comments 🙂
Hi. I previously asked if Linode uses HAProxy for this service? (And indirectly I guess I was wondering what other software/hardware is being use. My post is still awaiting moderation even though posts made after mine have been approved.
In the past Linode has been quite open about its architecture, especially about its implementation of Xen. Is there a reason we don’t get much detail about how NodeBalancers work? Is there something offensive or inappropriate about me asking these things?
Tom, I’d be interested too… Although it’s not out of the realm of possibility that they built their own with something like Golang (esp since 1.1), an accounting proxy would be trivial on such stack.
Any chance to have TLS renegotiation so we can host more than one domain on HTTPS ?