HashiCorp Vault is an open source, centralized secrets management system. It provides a secure and reliable way of storing and distributing secrets like API keys, access tokens, and passwords.
Deploying a Marketplace App
The Linode Marketplace allows you to easily deploy software on a Compute Instance using the Cloud Manager. See Get Started with Marketplace Apps for complete steps.
- Log in to the Cloud Manager and select the Marketplace link from the left navigation menu. This displays the Linode Create page with the Marketplace tab pre-selected.
- Under the Select App section, select the app you would like to deploy.
- Complete the form by following the steps and advice within the Creating a Compute Instance guide. Depending on the Marketplace App you selected, there may be additional configuration options available. See the Configuration Options section below for compatible distributions, recommended plans, and any additional configuration options available for this Marketplace App.
- Click the Create Linode button. Once the Compute Instance has been provisioned and has fully powered on, wait for the software installation to complete. If the instance is powered off or restarted before this time, the software installation will likely fail.
To verify that the app has been fully installed, see Get Started with Marketplace Apps > Verify Installation. Once installed, follow the instructions within the Getting Started After Deployment section to access the application and start using it.
Estimated deployment time: Vault should be fully installed within 5-10 minutes after the Compute Instance has finished provisioning.
Configuration Options
- Supported distributions: Debian 11, Ubuntu 22.04 LTS
- Recommended plan: We recommend a 4GB Dedicated CPU or Shared Compute instance for the Vault instance.
Limited User (Optional)
You can optionally fill out the following fields to automatically create a limited user for your new Compute Instance. This is recommended for most deployments as an additional security measure. This account will be assigned to the sudo group, which provides elevated permission when running commands with the sudo prefix.
- Limited sudo user: Enter your preferred username for the limited user.
- Password for the limited user: Enter a strong password for the new user.
- SSH public key for the limited user: If you wish to login as the limited user through public key authentication (without entering a password), enter your public key here. See Creating an SSH Key Pair and Configuring Public Key Authentication on a Server for instructions on generating a key pair.
- Disable root access over SSH: To block the root user from logging in over SSH, select Yes (recommended). You can still switch to the root user once logged in and you can also log in as root through Lish.
Getting Started after Deployment
Obtaining the Unseal Key
The data within Vault is protected by a series of encryption keys. The first layer is an encryption key stored in the keyring. The keyring is then encrypted using the root key. And lastly, the root key is encrypted using the unseal key. The unseal key is split into multiple portions, which can then be distributed to multiple people. This process ensures the data is protected and only authorized users can gain access. See Seal/Unseal documentation to learn more about this encryption process.
Follow the instructions below to view the unseal key and root token.
- Log in to your Compute Instance via SSH or Lish using the root user credentials you created during deployment.
- Run the following command to display all five portions of the unseal key. These portions can be used together to decrypt the root key and unseal Vault.
cat /root/.vault_tokens.txtUnseal Key 1: M8H0MQbg5Vgdf5IFEL/xOvyBC0bXwH+exN9wLgSwyq1y
Unseal Key 2: oP7fCkpdJXrO/AegtuUtQAiiyK//fhPtfyfFzEnT5z8b
Unseal Key 3: dSB00TzKHK9Nq5S+w2zWDzlokxMhYnUx6xNXXFuXHw9o
Unseal Key 4: UJEqMsSKbtGM1SZNJjUmx0/V7Q4g5pI63V0aRIulHVm3
Unseal Key 5: UMBRh+13zGwYgTIunTl6F0qJRoWW4JS6U5WzazwAhOoz
Initial Root Token: hvs.z1f4cwvE9llTjBmkJO71xhF4 - Distribute the portions of the unseal key to your team as needed, making sure they are saved in a safe and secure location. In addition, save the Initial Root Token. After you are finished, you can delete this text file.
rm /root/.vault_tokens.txt
Accessing the Vault Web UI
- Open your web browser and navigate to
http://[ip-address]:8200, where [ip-address] is your Compute Instance’s IPv4 address. See the Managing IP Addresses guide for information on viewing IP addresses. - To access the Vault instance, three of the unseal keys must be entered along with the root token.
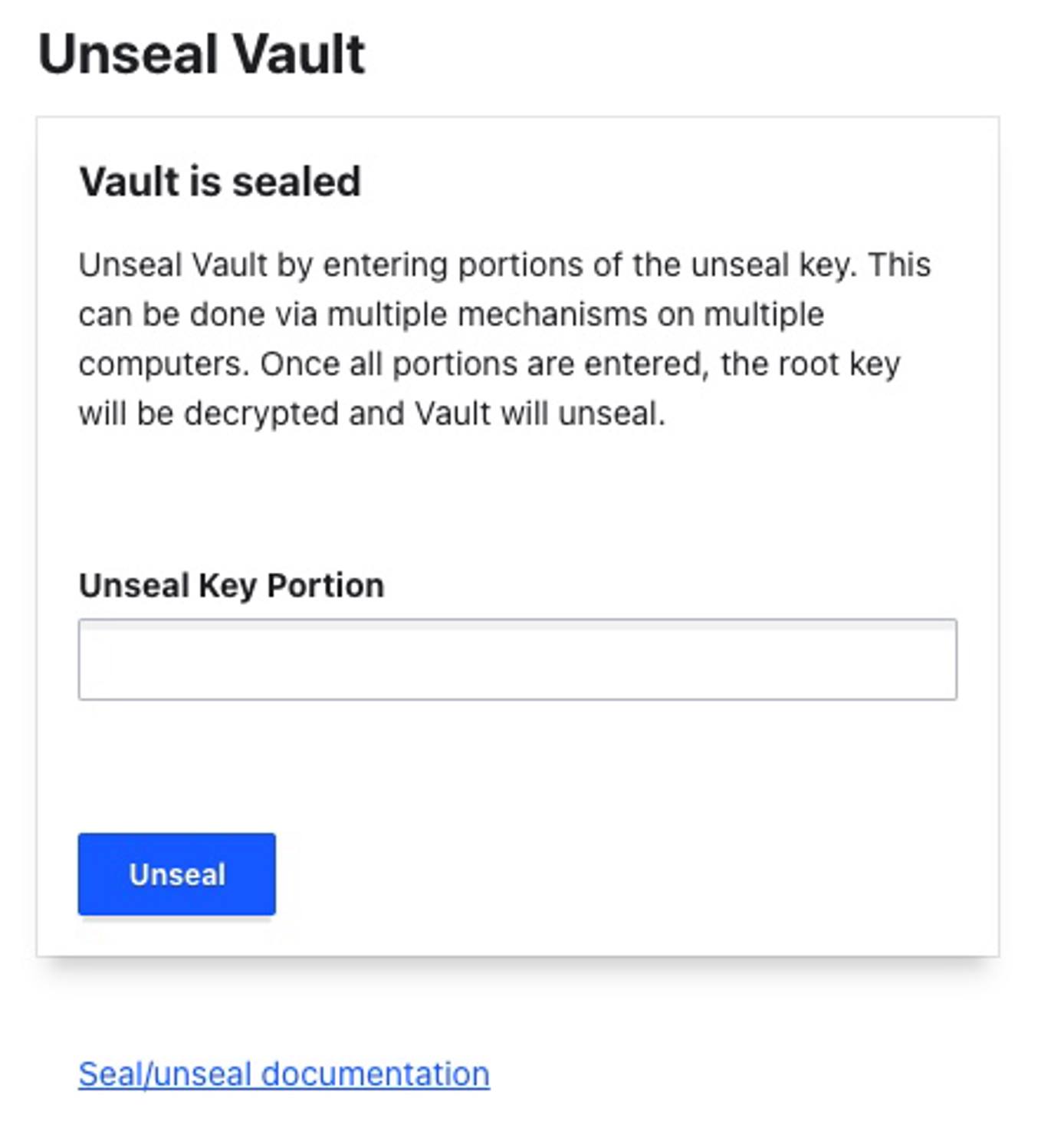
- Once the Vault is unsealed, the web UI can be used to set up secrets, authentication, and policies.
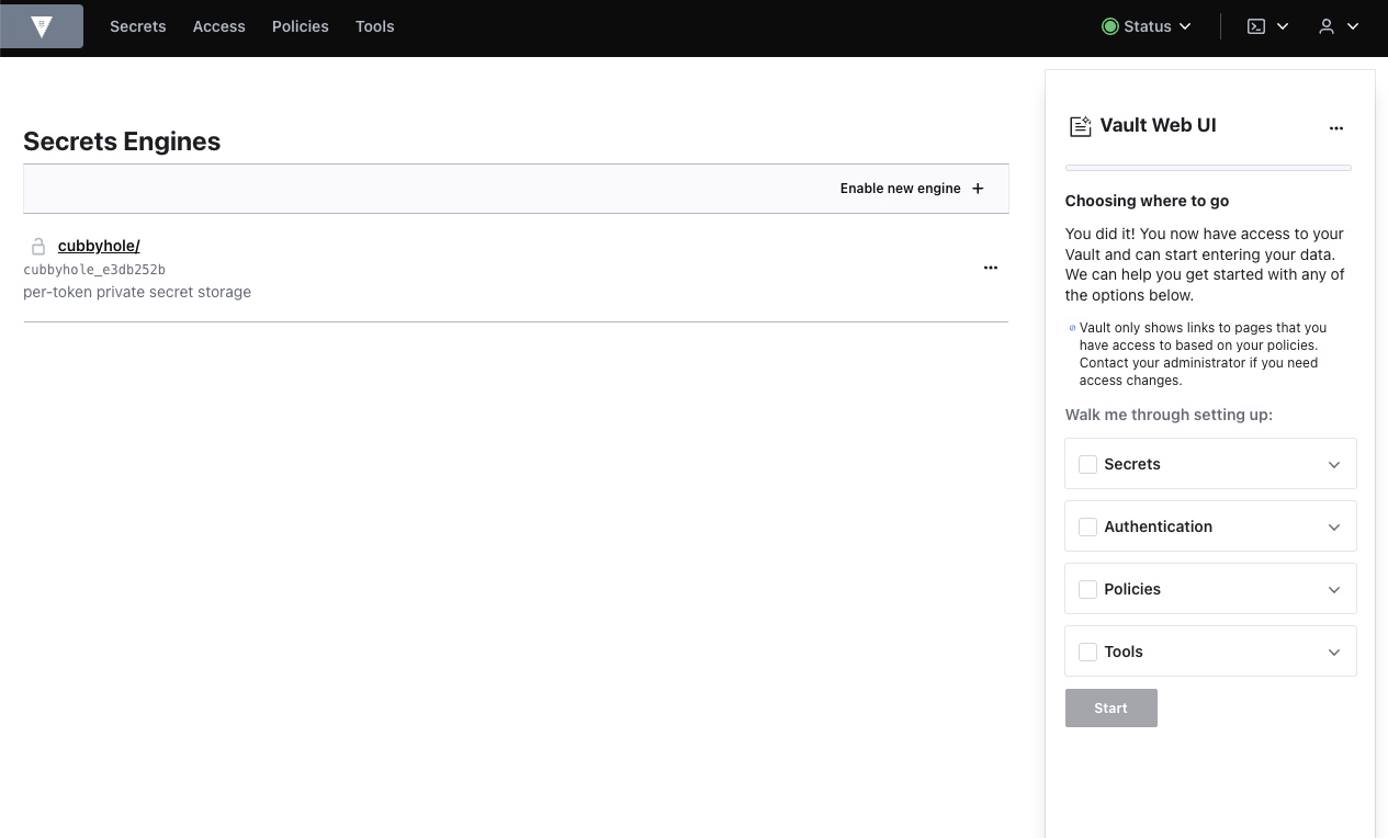
Note: HashiCorp recommends using mutual TLS (mTLS) with a private CA to secure cluster communications and the web UI. Please see the following HashiCorp documentation for more details. https://www.vaultproject.io/docs/auth/cert https://www.vaultproject.io/docs/secrets/pki/setup - Additional configurations are required to use the Linode Marketplace Vault instance in a production environment. We recommend reviewing the Configuration, Secrets Engine, and Authentication documentation before proceeding further.
The HashiCorp Vault Marketplace app was built by Linode. For support regarding app deployment, contact Linode Support. For support regarding the tool or software itself, browse the Vault Community Forum.

