Today, we’re here to talk about the Border Gateway Protocol (BGP) and a recent step we’ve taken towards securing it in our networks. While we’ve been signing our prefixes with Route Origin Authorizations (ROAs) for a while, we implemented route validation on all our edge gateway routers worldwide and are now dropping RPKI-invalid prefixes.
To understand the change, we need to understand how the TCP protocol works. BGP is one of the protocols that make the internet work. The internet is a vast network of networks. These independent networks have their own IP address ranges provisioned by the Regional Internet Registries (RIRs). These ranges are what BGP refers to as Prefixes.
Next, these prefixes are grouped together in an abstract system called the Autonomous System (AS), identified by a number called the Autonomous System Number (ASN). Finally, the BGP speaking edge router of every independent network is called a Peer. For BGP to function, each peer exchanges routing information with its neighboring peers in the form of network prefix announcements. Since peers may exchange all of the routes they have depending on routing policy, an AS doesn’t need to be directly connected with another AS to learn its prefixes. In such a case, the intermediary AS serves the purpose of a transit AS exchanging routing information with the edge ASes.

BGP Hijacking
False advertisement of prefixes that one does not control, whether intentional or accidental, is called BGP hijacking. The result of which involves various types of attacks like DDoS, monitoring, spam, and more.
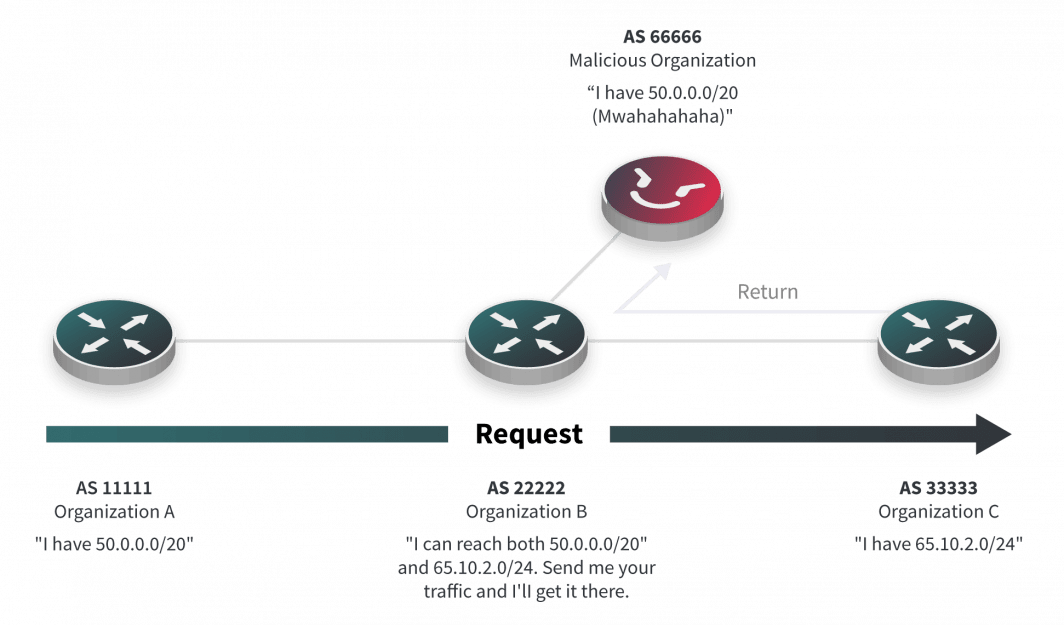
For a BGP hijack attack to be successful, other networks must select the hijacked path as the best path in one of the following ways:
- Since BGP generally prefers the shortest AS path length, the adversary might offer a shorter AS path length than the legitimate prefix owner. Other BGP attributes can also be used to prefer a path, but this behavior is very much dependent on the routing policies of an ASN.
- The adversary must announce a more specific prefix than what may be announced by the true originating AS. Prefix length-based hijacks are more likely to succeed as they don’t rely on potentially complicated BGP policies.
While the attack complexity is quite high for such an attack to succeed, BGP hijacking is nearly impossible to stop without some form of authorization. And that’s where RPKI comes into play.
RPKI
Think of RPKI as digital signatures; it provides an attestation that BGP speaking routers accept only certain Autonomous Systems that are authorized to originate particular prefixes. Essentially, with RPKI, BGP route announcements issued from a router can be signed and validated based on the ROA certificate to ensure that the route is coming from the resource holder and that it is a valid route.
With RPKI enabled in our networks, we sign our route prefixes with the ROAs and drop BGP advertisements from sources with invalid RPKI signatures. This acts as a preventative measure against many threats associated with BGP hijacking, including DDoS, spam, phishing, data monitoring, and more.
We’re doing our part to make the internet a safer place. To learn more about RPKI, refer to this documentation from ARIN.
If you’re interested in some stats, here’s a cool RPKI monitor from NIST.






Comments