For applications of all sizes running in the cloud, security is a shared responsibility model. Your cloud provider ensures a level of security at the broader network and host levels, but when it comes to protecting your workloads, every developer needs to understand the layers of security that are available.
What is a WAF?
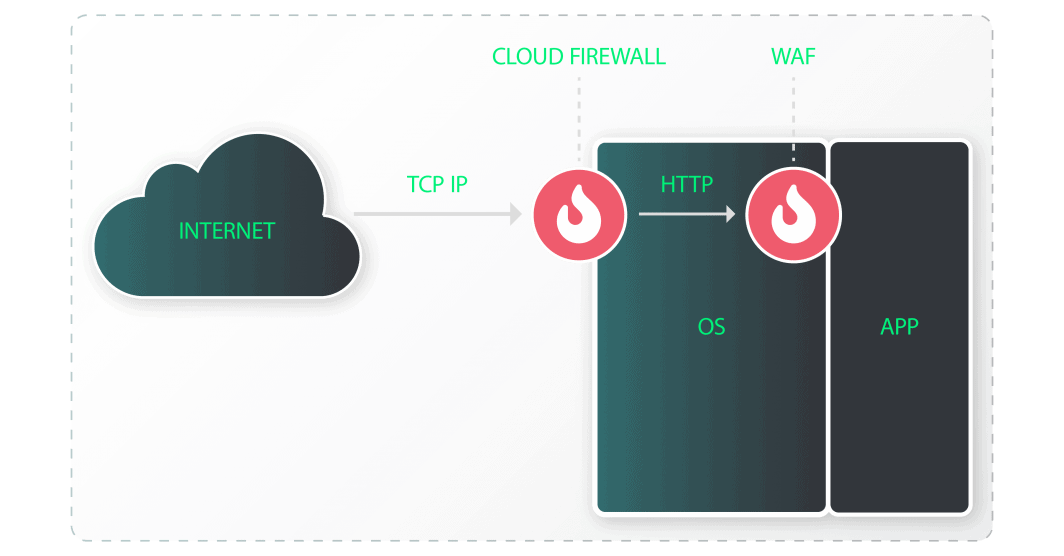
A web application firewall (WAF) prevents malicious traffic from interacting with an application and protects data from unauthorized access. Not to be confused with our Cloud Firewall that creates a layer of protection at the TCP/IP level, a web application firewall’s purpose is to create fine-tuned rules and behavior detection to protect what type of traffic can actually reach the application layer. Web applications are vulnerable to attacks like cross-site scripting and SQL injections that can bypass broader network level security configurations.
Here’s a real world comparison. A WAF is similar to the role of building security when you’re entering a building as a guest. Security proceeds to…
- Inquire about your purpose for entry
- Admit or deny access to specific building areas with a badge or guest pass
- Be on alert for any suspicious behavior while you’re in the building
- Collect your badge on your way out
- Note when you exited
For an application with a WAF, the security guard represents the basic behavior and goals of the WAF, but for monitoring web traffic.
When to Use a WAF
As your application evolves, you might start handling a higher volume of data and different classes of sensitive data. Here are some important questions to consider when looking into improving your application security and deciding how you need to implement your security solutions.
- How does your application use data?
- What kind of data are you handling?
- What other networks have access to the data that you handle?
- What would happen to your users if there was a data breach?
This is especially relevant for handling personal identifiable information (PII). PII can be a single piece of data,like a passport ID number, or several pieces of data that can reveal a person’s identity, such as the combination of someone’s full name and birth date.
A WAF isn’t always necessary. If you have a simple application that doesn’t deal with any financial transactions, only collects a user’s email, and requires encrypted passwords to access content, it’s probably not essential that you run a WAF. Take a basic calendar or appointment scheduling application; a WAF wouldn’t further secure this basic information.
If you’re running a small application with a moderate amount of PII transactions, implementing a WAF can be valuable. Even a moderate transaction volume has the potential of being specifically targeted by bad actors. In addition, if there’s any expectation to scale your application, having a WAF in place will secure your user’s data and reduce the level of effort to increase your transaction volume in the future.
For high-volume ecommerce or other applications that process and store large amounts of sensitive information, more security is needed. This includes implementing a robust WAF. These kinds of applications are the heavy hitters you might think of when it comes to data that needs powerful protection: financial institutions, healthcare providers, and government entities.
Selecting a WAF
Choosing a WAF depends on two key factors: the level of compliance required by the data your application handles, and whether your workload is best suited for a self-managed solution versus handing all the control to a trusted security company that has the necessary expertise and compliances.
Just like other technology services, WAF solutions are a mix of self-managed and vendor-managed solutions. There are free open source WAFs that require management and updates, which is a good fit for developers who want a fine-tuned level of control.
Larger workloads and applications that handle sensitive data benefit from vendor-managed solutions that are actively updated based on the most recent threat intelligence and potential vulnerabilities. Reputable cybersecurity companies list and maintain their levels of compliance, which will determine whether their products are in compliance when interacting with your application. This is the same consideration for choosing a cloud provider to host the application and data itself.
Different WAF solutions include additional features like the depth of monitoring, including the ability to get real-time updates), log retention, and integrations with the rest of your tech or business stack.
Find the Right WAF Solution
We offer different levels of WAF solutions so you can find the right match whether you’re just getting started with an open source self-managed solution, or your application requires powerful protection.
For a fairly basic WAF that protects your application from major attacks and provides some monitoring, the Haltdos Community WAF is an excellent place to start. Haltdos is a self-managed solution with an intuitive GUI where you can see the volume of incoming requests, IP addresses, and the top attacking IPs to monitor for risk.
Deploy via Linode Marketplace | Install on an Existing Resource | Learn More
For enterprise workloads and larger applications that handle PII, Akamai’s App & API Protector shields applications and API networks from a wide range of threats, including vulnerabilities in the OWASP API Security Top 10. App & API Protector uses machine learning analysis and data from Akamai’s threat intelligence and mitigation teams to bolster security on an ongoing bases, keeping up with security threats, standards, and demands.








Comments